Exposure management is becoming a central theme for organisations that want to move beyond traditional vulnerability workflows. At Nomios, we see this shift every day. As a Tenable partner, we help organisations adopt Tenable One, whether fully cloud delivered or deployed on-prem, and we support teams throughout the rollout. For organisations that prefer to outsource operations entirely, our Managed Exposure Management service takes ownership of the platform and day-to-day exposure reduction.
This article walks through the exposure management maturity model and how we help organisations progress from basic scanning to data-driven exposure reduction.
Why many organisations stall in their security maturity
Across industries, most security teams follow similar patterns. They invest in more tools, add more processes and hire specialists for each domain. Yet even strong programmes hit a ceiling. They struggle to scale, duplicate effort across silos and still miss the relationships between assets, identities and misconfigurations that attackers rely on.
The core issue is fragmentation. Each domain operates with its own data set, its own dashboards and its own priorities. Findings increase while context stays thin.
Exposure management addresses this by pulling data together and adding relationship context. It gives teams a broader view of their attack surface and helps them act on what actually matters.
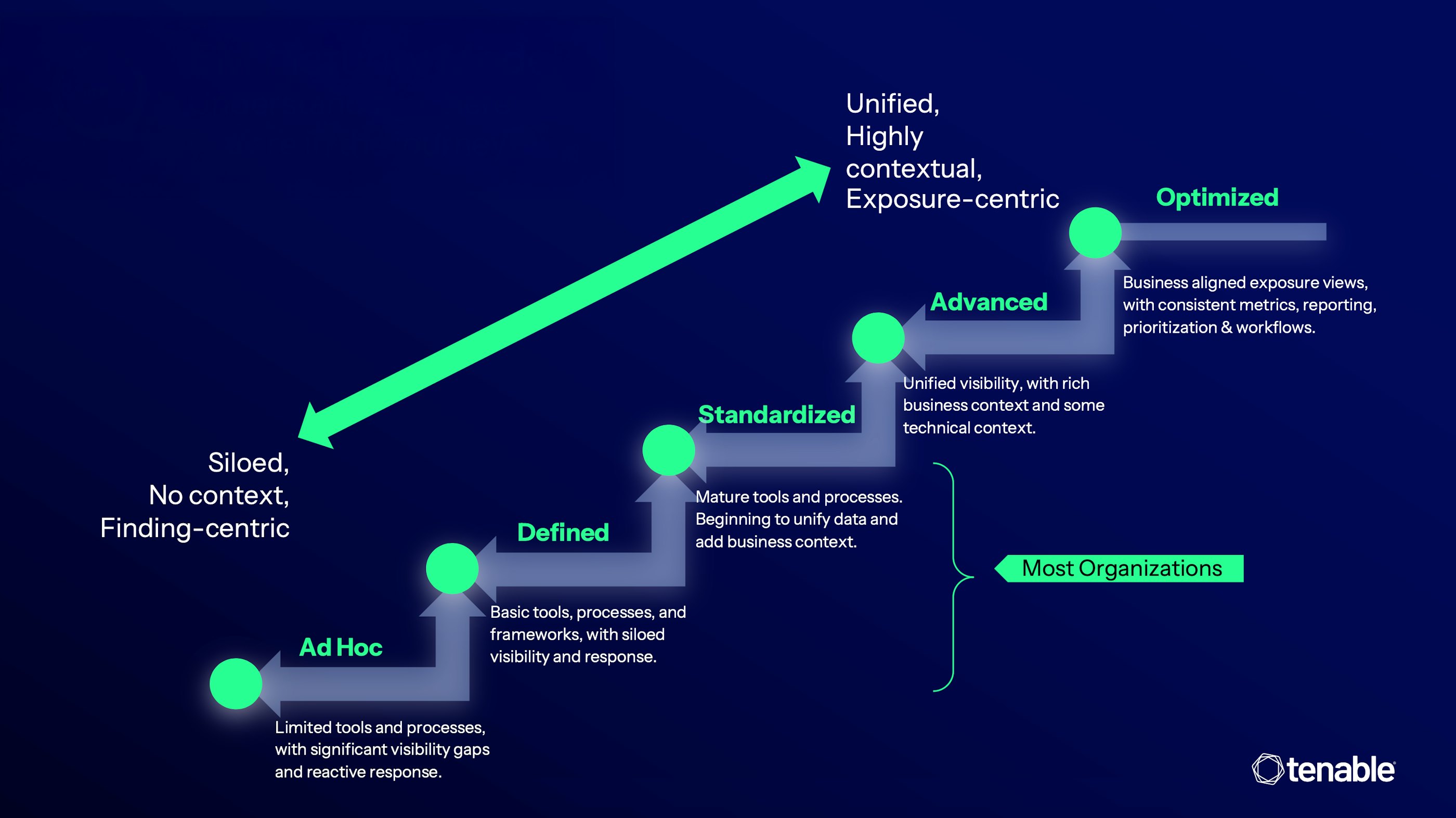
The five stages of exposure management maturity
Stage 1: Ad hoc
Security is informal and reactive. Tooling is basic, often limited to free scanners or functionality inside IT tools. Scans run infrequently, visibility is patchy and the focus is keeping things running rather than reducing exposure. Processes are rarely documented.
Stage 2: Defined
Teams introduce dedicated tools such as vulnerability management or web application scanning. Processes are documented, but data still sits in silos. Coverage across cloud, SaaS, OT and IoT is inconsistent. Analysts spend time correlating findings manually because the context to prioritise is lacking.
Stage 3: Standardised
This is where many mature organisations level off. The toolset is broad, often best-of-breed per domain. Processes are established and automation is improving. Organisations apply tagging and risk-based vulnerability management to align to business priorities.
Yet even with strong tooling, scaling becomes difficult. Data remains fragmented, procurement becomes complex and teams struggle to connect findings across domains.
Stage 4: Advanced
The shift to Advanced maturity starts with unifying asset and risk data. Some teams attempt this through CAASM or UVM tools, others by exporting everything into a data lake. Unification is only the first step. Maintaining BI-style infrastructure is expensive and outside most security teams’ core skill set.
Exposure management platforms solve this. They create a single, consistent view of the attack surface by collecting and normalising data from multiple sources. Teams get a unified approach to scoring, reporting and workflow, which cuts operational overhead and reduces duplication.
Stage 5: Optimised
At the highest maturity level, organisations integrate technical and business context. Exposure management platforms use AI to map how assets, identities and misconfigurations relate to each other and how attackers move across them.
Instead of chasing individual findings, teams focus on choke points with the biggest blast radius. Prioritisation accounts for threat activity, exploitability, access paths and business impact. This allows large-scale reduction of exposure with far less effort.
Exposure management enters the Gartner Magic Quadrant
Recently, Gartner published the first Magic Quadrant for Exposure Management. For us, this is a clear sign that the market is moving beyond traditional vulnerability workflows and recognising exposure management as its own category. The fact that a major analyst now tracks this segment confirms what we already see with our clients: organisations want a unified view of their attack surface, consistent prioritisation and a more practical way to reduce real business risk. The release of this Magic Quadrant shows that exposure management has matured into a defined market with clear leaders, approaches and expectations.
How Nomios supports your maturity journey
As a Tenable partner, we help organisations adopt exposure management at their own pace. Our services include:
Advisory and architecture
Mapping your current maturity stage and defining the target state.
Deployment support for Tenable One
Whether cloud-based (Tenable One T1) or on-prem, we assist with rollout, configuration and integration with existing security tooling.
Managed Exposure Management
For organisations that want outcomes rather than platform upkeep, our MSSP team operates the entire Tenable One environment. We handle scanning strategy, attack path review, prioritisation, workflows and continuous tuning.
Ongoing maturity development
We help teams expand coverage, improve context, integrate new data sources and adopt exposure-led processes.
If you want to benchmark your organisation, Tenable provides a short online exposure management maturity assessment that gives an initial indication of where you sit and what to focus on next.
Our team is ready for you
Do you want to know more about this topic? Leave a message or your number and we'll call you back. We are looking forward to helping you further.