Cybersecurity is not “set-and-forget”. It’s a living ecosystem where something shifts every week: new cloud and AI capabilities, new attack techniques, new compliance requirements… and meanwhile consolidation keeps rolling on, with acquisitions constantly reshaping the landscape. The result? Roadmaps move, product names change, portals seem to multiply overnight, and before you know it you’re mainly managing… the lack of visibility.
If that sounds familiar: welcome to the club.
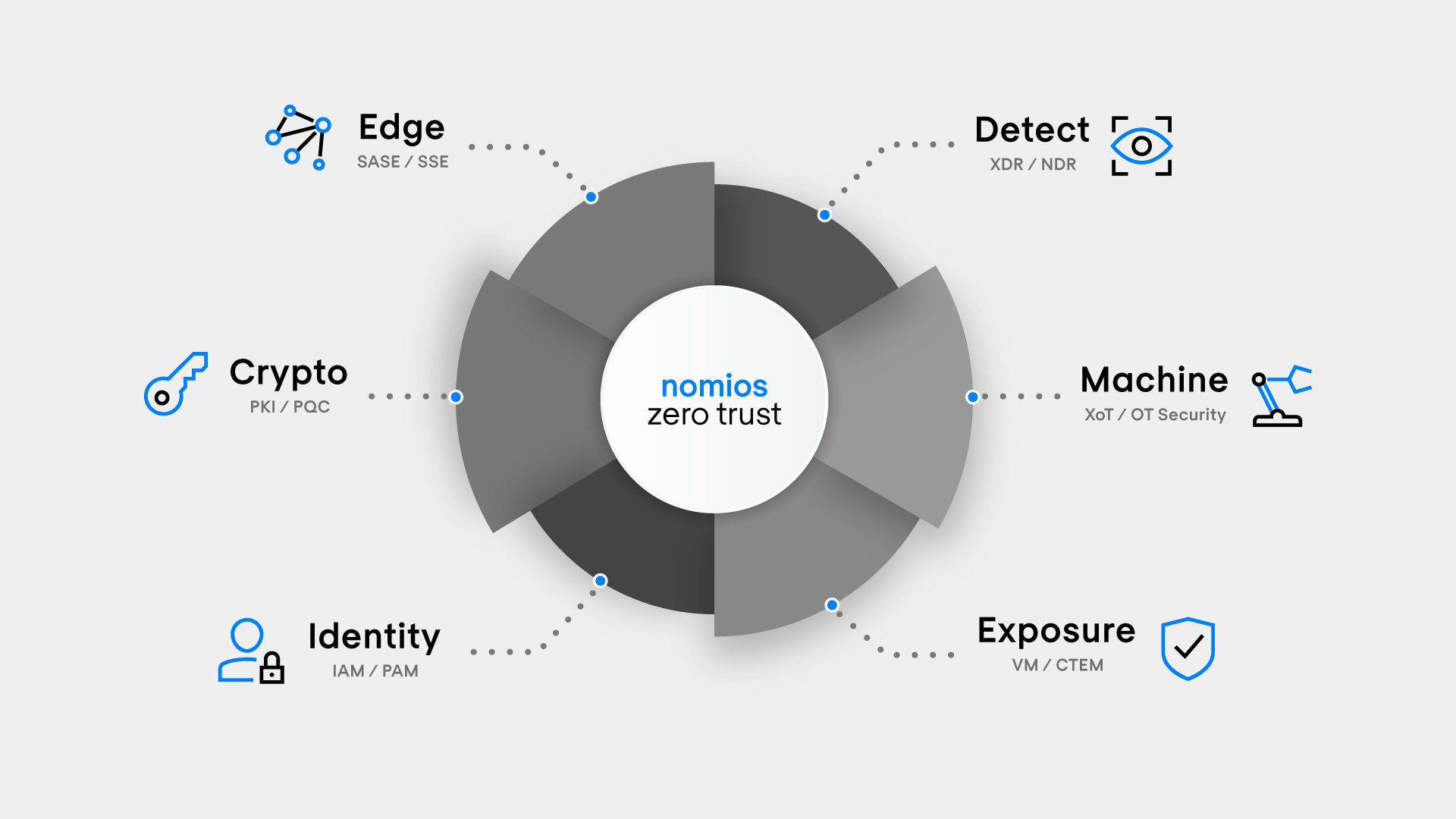
That is exactly why Nomios is introducing a refreshed cybersecurity portfolio that doesn’t start from individual products, but from an architecture. A portfolio that provides grip in a dynamic market while staying practical: from strategy and design through to implementation and operations. You can see the essence of it in our visual: six domains coming together as one — Nomios Zero Trust.
Six domains, one Zero Trust architecture
Zero Trust is sometimes sold as if it’s a product you can simply “switch on”. If only. In practice, Zero Trust is a coherent set of design choices: how you connect identity, access, segmentation, detection, exposure management and cryptographic assurance into a single, consistent approach.
Nomios is one of the few MSSPs in Europe with deep expertise across all six relevant domains — and that combination is what makes the difference. In the visual, Nomios Zero Trust sits at the centre. Around it, six building blocks form a complete model:
Edge (SSE / SASE)
The edge is where users, devices and workloads “touch the internet” — and where policy must be enforced, regardless of location. With SSE/SASE, you bring access, web security and (cloud) network controls together, so you’re no longer dependent on where someone is, but on who they are, what they’re doing, and in which context. In practice, Zero Trust often starts here: access that isn’t implicitly trusted, but continuously evaluated.
Detect (XDR / NDR)
Prevention remains essential, but detection determines how quickly you can truly respond. With XDR/NDR, you combine signals from endpoints, networks, identities and cloud environments into a single detection and response capability. The value isn’t in “more alerts”, but in better correlation, faster triage and more effective response. Because, let’s be honest: an inbox full of warnings is not a SOC strategy.
Crypto (PKI / PQC)
Cryptography is the quiet foundation of digital assurance: authentication, integrity, encryption, signing, machine-to-machine trust. With PKI you ensure identities (human and machine) are verifiable and that trust can scale. And with PQC (Post-Quantum Cryptography) you prepare for the moment when classical algorithms come under pressure. Crypto agility is crucial here too: the ability to replace cryptographic algorithms and keys quickly and in a controlled way as threats, standards or requirements evolve. Crypto is therefore not a niche; it is a core layer under Zero Trust — especially as we move towards 2026.
Machine (XoT / OT Security)
The scope of “what you need to protect” is no longer just IT. XoT and OT bring different risks, different availability requirements and often very different lifecycles. You can’t treat OT like a fleet of laptops (and you really don’t want to find out why during an incident). Zero Trust for Machine means: visibility, segmentation, secure access, monitoring and an approach that fits operational reality.
Identity (IAM / PAM / IGA)
Identity is the decision engine of Zero Trust. IAM determines who can request and use access, PAM controls privileges (where the crown jewels are), and IGA provides governance: access rights that are correct, processes that are auditable, and a lifecycle that remains manageable. In modern environments, identity isn’t “a component” — it is the control plane.
Exposure (VM / CTEM / ASM)
Zero Trust without exposure management is like an alarm system without locks: you’ll notice something, but it’s too late. With VM (Vulnerability Management) you address vulnerabilities, with CTEM (Continuous Threat Exposure Management) you steer based on risk and attack paths, and with ASM (Attack Surface Management) you map your external and unknown surface area. This domain ensures you don’t only respond, but improve structurally over time.
These six domains reinforce each other. Edge and Identity govern access, Crypto makes trust verifiable, Detect sees what is happening, Exposure prioritises what will really hurt, and Machine ensures that “non-IT” is also part of your security model. That interplay — not any single tool — is what we mean by Nomios Zero Trust.
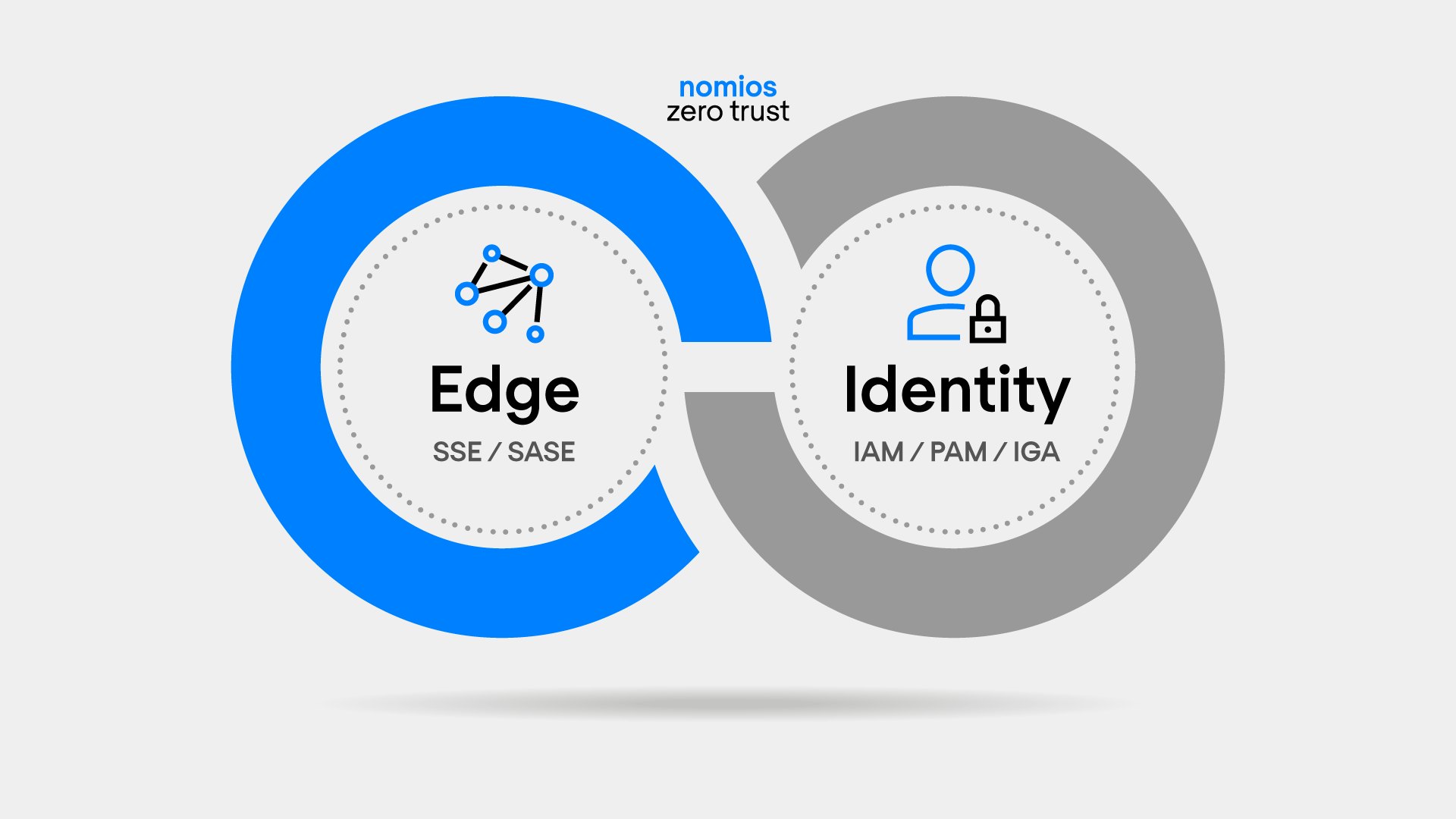
Universal Zero Trust, with a unique unified security fabric
Nomios delivers a Universal Zero Trust Architecture: vendor-independent by design, pragmatic in execution, and focused on measurable risk reduction. No “rip-and-replace”, but a cohesive architecture that works with the reality of hybrid environments, existing investments and (yes) organisational constraints.
What sets us apart is the combination of Edge with Identity and Crypto at a high level. Thanks to the expertise of Intragen within Nomios, we bring identity-driven security together with the other domains into a unified security fabric: one coherent trust layer that connects policies, access, certificates, keys and governance.
From architecture to operations: services that deliver business value
A portfolio only creates value if you can implement it and run it. That’s why the renewed Nomios portfolio isn’t just domain expertise — it also includes a clear services model, designed to help organisations step by step towards higher security maturity.
Consulting services
For strategy, target architecture, roadmaps, risk-based prioritisation and governance. Think Zero Trust design, assessment & maturity programmes, exposure-driven roadmaps, compliance translation (what does regulation actually require for your organisation?), and decision-making that goes beyond “we still have some budget left”.
Professional services
For implementation and integration. From SSE/SASE design and onboarding, to XDR/NDR use cases, OT segmentation, IAM/PAM/IGA programmes and PKI implementations. This is where architecture becomes “real” — including the less glamorous parts, like integrations, migrations and operationalisation.
Managed services
For continuous operations and optimisation. Monitoring, detection, response support, platform management and continuous improvement. Not as a separate management layer, but as an extension of your security model: what you design must also work consistently in day-to-day reality.
For organisations looking to measurably raise their security maturity in 2026, this is the combination that matters: architecture + implementation capability + operational maturity.
Six themes that will shape 2026
Priorities are shifting. Not because “trends” say so, but because the underlying forces are changing: geopolitics, faster technology cycles, AI-driven attacks, stricter regulation and more complex supply chains. These are the themes we expect to be front and centre for customers in 2026 — and they connect directly to Nomios Zero Trust:
Digital sovereignty
Control over your digital trust anchors is becoming strategic. PKI plays a key role here: certificates, signing, encryption, lifecycle management and governance. Whoever controls the keys ultimately decides who — and what — can be trusted.
Quantum security (PQC)
PQC is no longer a “future problem”, but a migration journey that requires preparation: crypto inventory, use cases, hybrid approaches, vendor choices and impact analysis. You don’t need to change everything tomorrow, but in 2026 you do want to know where you stand — and how you will migrate.
Convergence of SSE and IAM
Access is increasingly identity-first and policy-driven. The line between “network security” and “identity security” is fading. Organisations that design SSE and IAM as one coherent control plane win: fewer gaps, better user experience and stronger auditability.
Scalable Security Operations
More telemetry is not the same as more security. It’s about better detection, faster response and measurable improvement cycles. XDR/NDR, use-case engineering and exposure-driven prioritisation will be key drivers of effectiveness.
AI in cybersecurity
AI accelerates attacks (phishing, social engineering, exploit development) and defence (triage, analytics, automation). But it also requires governance: which AI can be used for what, how do you prevent data leakage risks, and how do you avoid “AI” becoming a black box in decision-making?
Supply chain risk and compliance (NIS2, DORA and more)
The supply chain is both an attack vector and a compliance topic. NIS2 and DORA raise the bar for risk management, reporting, resilience and demonstrability. Zero Trust helps — but only if you translate it into controls, processes and operational execution.
In closing
The market will keep moving. That’s a given. The real question is whether you move with it in a way that increases complexity — or in a way that makes your security model stronger and more coherent.
With the renewed Nomios cybersecurity portfolio, we bring six domains together in one Nomios Zero Trust approach — and deliver a universal architecture you can design, build and run. With an additional differentiator: the unified security fabric created by the combined strength of Edge, Detect, Identity and Crypto. If you want 2026 to be about more than “keeping up”, now is the time to put your Zero Trust foundations in place — before the next wave of acronyms rolls in.
Our team is ready for you
Do you want to know more about this topic? Leave a message or your number and we'll call you back. We are looking forward to helping you further.