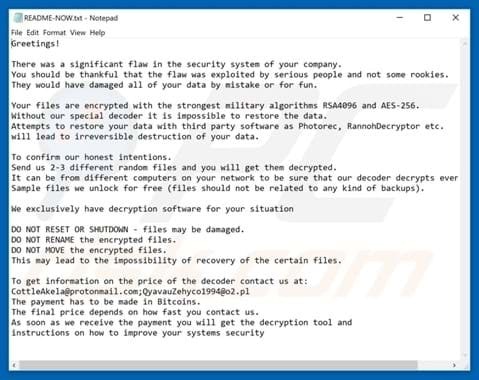
Ransomware is malicious software used to encrypt computer systems, files and personal information. Once infected by ransomware, a message or ‘ransom note’ is displayed demanding payment for decryption.
Usually, the ransom has to be paid within a certain period of time. Missing the deadline could result in cybercriminals increasing the amount of the ransom, or the decryption key being allegedly destroyed.
How is ransomware installed and how does it work?
Ransomware is a type of malware created by individual cybercriminals or cyber threat groups. Ransomware can be installed using multiple tactics such as misleading links in email messages, chat messages, text messages (SMS) or websites. The malware of the type ransomware can not only lock computers or encrypt files on just one end-station, it could also spread throughout an organisation. Getting your workstations infected with Ransomware is one thing, but losing all your files and backups is quite another.
Ransomware payments
Ransomware always requires a payment (ransom) to be paid for supposed decryption. Payment methods offered vary from payments through cryptocurrency such as Bitcoin, or through credit cards or untraceable gift cards. However, paying the ransom does not ensure the organisation or user regains access to the encrypted system or files. Paying the ransom could even motivate cybercriminals to target the same victim(s) again.
Best practices for ransomware security and prevention strategies:
In order to successfully defend against ransomware, security strategies cover a wide area of measures that need to be taken.
1. Educate employees on cybersecurity and show them ransomware examples regularly to raise awareness by:
- Ensuring employees know how to create strong passwords and manage them in a secure way
- Organising training sessions to educate employees on what ransomware is and what to look for before engaging with malicious content
- Sharing examples and screenshots of emails, chat messages and other methods used to mislead users convincing them to unknowingly click or install malware
- Having employees connect to your corporate secure wireless connections only
- Monitoring and intercepting phishing emails on all endpoint devices using endpoint security and email security solutions
2. Patch and update operating systems and software at all time(s):
Minimise exposure to known vulnerabilities in software and operating systems by keeping them up to date. Hackers are always on the lookout for such opportunities to exploit. Monitor all endpoint devices to keep track of outdated versions of operating systems or software running inside your organisation. Ensure the latest patches are installed, update software and keep operating systems up to date to minimise threats.
3. Use cybersecurity software specialised in preventing unknown threats:
Traditional antivirus solutions are not enough to effectively defend against modern-day unknown types of ransomware. Cybercriminals have found different methods to bypass these legacy antivirus tools. Use next-generation antivirus and endpoint protection solutions rather than attempting to detect malware iterations known to legacy solutions.
4. Monitor endpoints and network environments for malicious activity and IOAs:
Effective endpoint detection and response (EDR) solutions are able to look for Indicators of Attack (IOAs), stopping ransomware ‘in its tracks’, before being able to execute and inflict damage.
If your organisation is not able to immediately act upon alerts and detected threats, consider Managed Security Services Provider (MSSP). The MSSP offers an elite team of experienced cybersecurity experts who proactively search for threats on your behalf 24/7. Among a wide variety of practices and technologies applied, the MSSP can also integrate threat intelligence feeds into your security strategy effectively. This enables your organisation to deploy countermeasures quickly and prevent malware from spreading.
Understanding the basics of cybersecurity
Get your copy of this 70+ pages whitepaper, to learn more about cybersecurity and to feel comfortable in a security conversation. Or get in touch with us directly if you find this topic of interest.