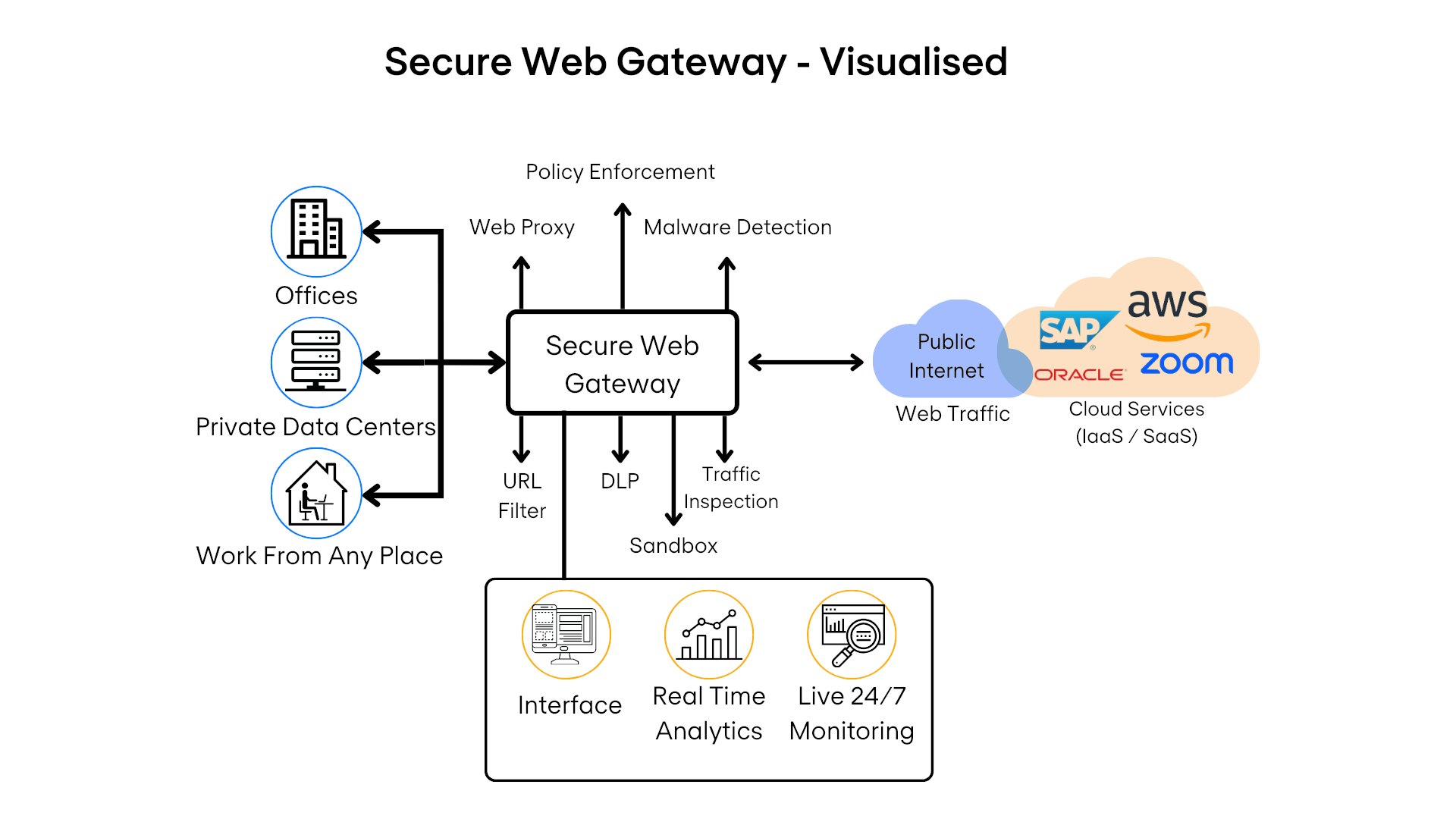
A Secure Web Gateway (SWG) is a pivotal security solution for organisations, serving as a barrier between users and the internet. It scrutinises all web traffic, ensuring adherence to security policies and protecting against threats such as malware, phishing, and other cyber-attacks.
SWG vs. Proxy: A comparative overview
Whilst both SWGs and proxy servers act as intermediaries between users and the internet, they differ markedly in purpose and capability. Proxy servers are primarily focused on managing internet traffic and enhancing network performance, offering basic web filtering and access control. However, their security features are somewhat limited.
In contrast, SWGs are centred on security. They provide comprehensive web filtering, antivirus scanning, Data Loss Prevention (DLP), SSL/TLS inspection, and Advanced Threat Protection (ATP), such as sandboxing. These capabilities enable SWGs to offer a more robust defence against cyber threats than proxy servers, making them essential for organisations that prioritise security, particularly those needing to comply with regulatory requirements, such as NIS2.
Key features of SWG
- URL filtering: Blocks access to malicious or inappropriate websites. This feature is essential for enforcing internet usage policies and protecting users from harmful online content.
- Malware protection: Detects and neutralises malware through signature and behavioural analysis. It proactively identifies known and emerging threats, ensuring real-time protection against malware.
- Data Loss Prevention (DLP): Monitors web traffic to prevent unauthorised data transfers. DLP is crucial for safeguarding sensitive information and ensuring compliance with data protection regulations.
- Application control: Manages the use of web-based applications following corporate policies. This allows organisations to control access to non-business-related applications, enhancing productivity and security.
- SSL/TLS inspection: Decrypts encrypted web traffic to unearth hidden threats. This is vital for comprehensive security as a significant portion of internet traffic is encrypted and could conceal malware or other threats.
- Advanced Threat Protection: Incorporates techniques like sandboxing to combat sophisticated attacks. ATP allows for the analysis of suspicious files and URLs in a safe environment, thereby preventing zero-day exploits and advanced persistent threats.
Handling encrypted traffic
Secure Web Gateways effectively manage encrypted SSL/TLS traffic through decryption, scanning, and re-encryption. This ensures the identification and blocking of threats concealed in encrypted connections, which is crucial, as a significant portion of web traffic is encrypted, and attackers often use encryption to hide malicious content.
Deployment options
SWGs can be implemented as hardware appliances, virtual devices, or cloud-based services. Each has its advantages and is suitable for specific organisational needs. Choosing the right option depends on factors such as existing infrastructure, security requirements, budget, and scalability needs.
Importance of scalability
A scalable SWG solution is essential to adapt to organisational growth, increasing bandwidth requirements, evolving threats, and technological advancements. It ensures uninterrupted protection and optimal performance, even as network traffic and the number of users increase.
Benefits for various organisations
SWG is advantageous for enterprises with a dispersed workforce, businesses in regulated industries, organisations using cloud services, SMEs, high-risk sectors, and e-commerce companies. It provides a consistent security level across different locations and for various types of users.
Integration with other security solutions
Integrating SWG with other security solutions, such as endpoint security, IPS, or SIEM systems, enhances threat detection, streamlines policy management, and establishes a robust, unified security strategy.
How Nomios can help
Nomios provides comprehensive advisory services and end-to-end managed network support, enabling organisations to align their technology choices with business objectives, address security and compliance issues, and implement effective change management processes.
Do you want to know more about this topic?
Our experts and sales teams are at your service. Leave your contact information and we will get back to you shortly.